Forensically Collecting Smartphone Data for Litigation
Lexbe’s forensic team is staffed with Cellebrite certified forensic experts that are highly adept at collecting evidence from Smartphones and other mobile devices.
Smartphones have become primary sources of evidence across all types of matters in litigation. As personal and professional productivity tools, Smartphones are often hubs of connectivity for access to cloud storage, social media, messaging, collaboration, email, data portability channels, and much more.
Here’s an example of the breadth of the data that can be forensically collected from a Smartphone.
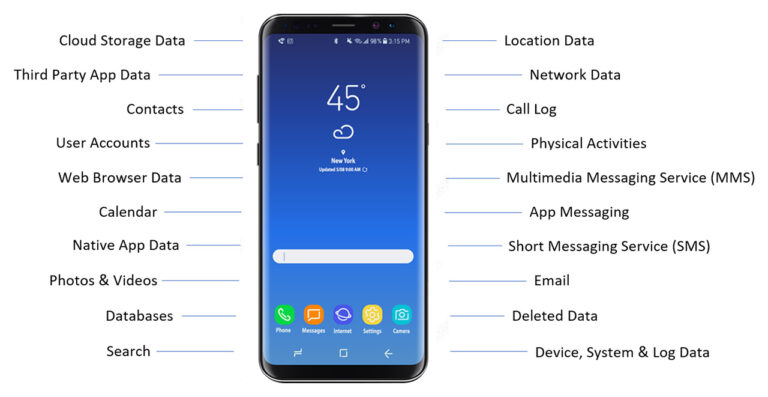

Discuss the scope of your matter with a digital forensic expert today, commitment-free!
Forensic Extraction Methods for Smartphones
At Lexbe, we utilize several extraction methods to collect the electronically stored information (ESI) from smartphones. The extraction method that is utilized is typically based on the collection parameters, including the availability of the device, credentials, and the scope of the investigation.
-
Physical Data Extraction
Extracts a physical bit-for-bit image of the flash memory of a device, including the unallocated space using advanced methods. Unallocated space is the area of the flash memory that is no longer tracked by the file system, which may contain deleted images, videos, files, and more.
-
Logical Data Extraction
Extracts user data from a mobile device (SMS, call logs, pictures, phonebook, videos, audio, certain application data, and more). This is the quickest extraction method but yields the least amount of data.
-
File System Extraction
Extracts files embedded in the memory of a mobile device. This method retrieves the artifacts within a logical extraction. In addition, this approach captures hidden system files, databases and other files which were not visible within a logical extraction.
-
Advanced Logical Data Extraction
Combines both the logical and file system extractions into a single extraction method for iOS and Android devices.
-
SIM Card Data Extraction
Extracts data from a Subscriber Identity Module (SIM) or Universal Subscriber Identity Module (USIM) card. This approach limits the scope of data that can be accessed.
-
Manual Data Collection
This process is very time consuming and requires a manual screen capture of the data and artifacts resident on the device.
-
Remote Data Collection from iPhones
Lexbe's forensic team utilizes the industry's most advanced tools to perform remote iPhone collections. This approach helps mitigate the inconvenience associated with custodians having to ship their phones for forensic collections.
State-of-the-Art Forensic Tools Help Make Sense of the Evidence on Smartphones
Lexbe’s forensic lab is equipped with the latest forensic tools that not only extract the data from smartphones but also help organize the data, including a timeline of activity that helps pinpoint activity on critical dates relevant to the case.
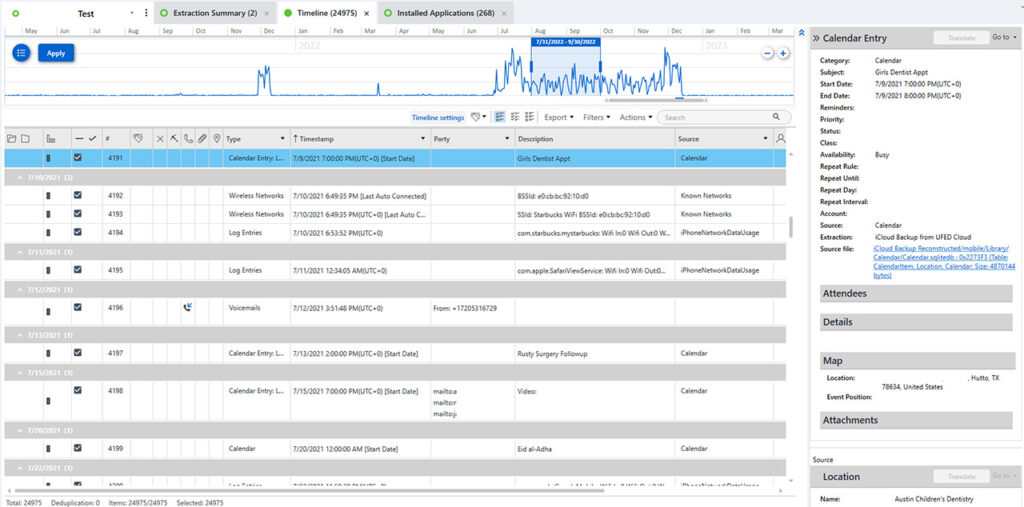
The forensic team at Lexbe is Cellebrite certified. Cellebrite is an industry leading smartphone forensic tool. In addition, the Lexbe forensic team utilizes industry best practices to ensure that each forensic collection is defensible and admissible in court.
Get a Complimentary Forensic Consult
If you have an upcoming matter or have questions about the identification and acquisition of evidence, then drop us a line. We’d be happy to schedule a complimentary call and discuss the matter with you and answer any questions that you have.
"*" indicates required fields
Learn More About Smartphone Forensic Collections

Anatomy of a Forensic Collection from a Smartphone
Learn critical evidentiary insights into smartphones as utilization skyrocketed due to the pandemic and their role in eDiscovery continues to grow.
